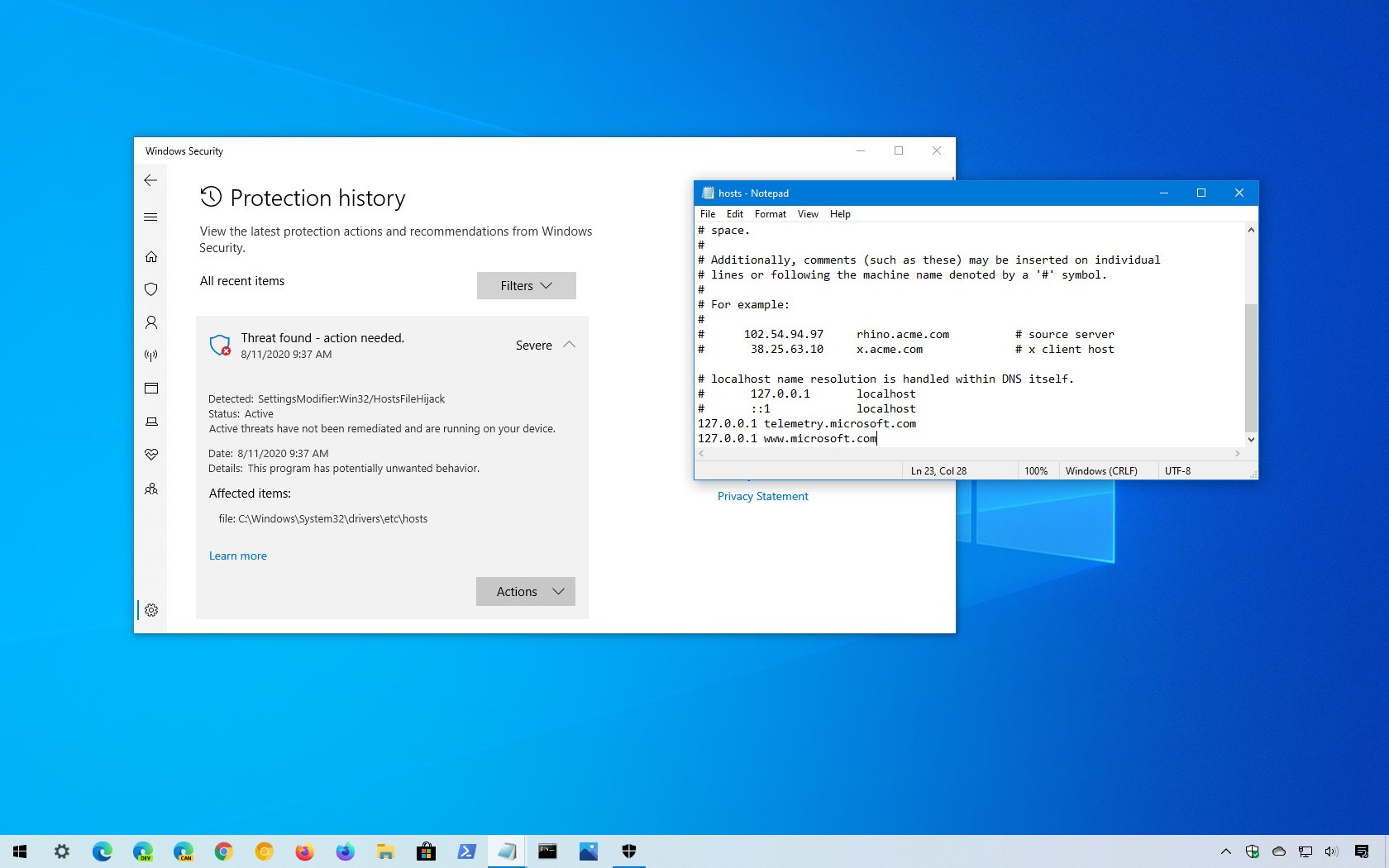
On Windows 10, the Microsoft Defender Antivirus now detects and flags the hosts file as a threat if it has unwanted redirects that blocks some of the company’s services, such as telemetry and updates (via BornCity).
The hosts file is a text file without extension that contains mappings for IP addresses to hosts or domain names. The file has been around for a long time, and users have been using it to create redirects and block certain online services manually.
According to a report from BleepingComputer, since July 2020, Microsoft Defender Antivirus detects the hosts file as malicious with certain redirects, and the details show up with a “severe” alert level and describes the threat as a program that has potentially unwanted behavior.
These are some of the domain redirects that the antivirus detects as malicious:
- www.microsoft.com
- microsoft.com
- telemetry.microsoft.com
- wns.notify.windows.com.akadns.net
- v10-win.vortex.data.microsoft.com.akadns.net
- us.vortex-win.data.microsoft.com
- us-v10.events.data.microsoft.com
- urs.microsoft.com.nsatc.net
- watson.telemetry.microsoft.com
- watson.ppe.telemetry.microsoft.com
- vsgallery.com
- watson.live.com
- watson.microsoft.com
- telemetry.remoteapp.windowsazure.com
- telemetry.urs.microsoft.com
It’s important to note that the default antivirus has been capable of detecting problems with the hosts file for years, but detecting telemetry and updates redirects as threat is recent.
Although the file can now be detected as malicious, you can still allow the changes using the Windows Security app. However, when you allow the file modifications, you’ll also be allowing possible future unwanted changes from other apps.
