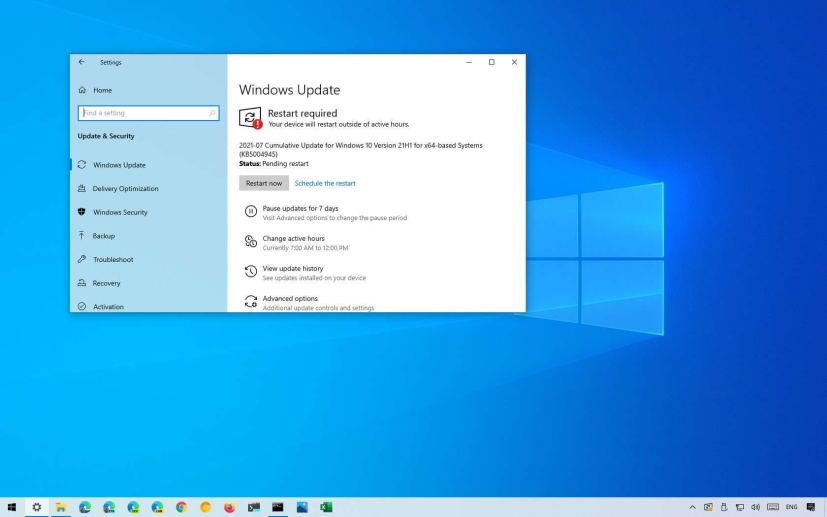
Outside of the regular schedule, Microsoft is now rolling out the update KB5004945 to fix the “PrintNightmare” vulnerability on Windows 10 21H1, 20H2, and 2004.
Recently, the software giant acknowledged a critical vulnerability described as CVE-2021-34527 that affects the Windows Print Spooler service, and it allows attackers to execute malicious code to create new administrator accounts, install programs, and access data without the user’s consent.
Immediately after confirming the vulnerability, Microsoft provided two workarounds to mitigate the issue, including the steps to disable the service temporarily and another set of instructions to set a Group Policy Object to block incoming connections to a print server.
The company has now released the update KB5004945 to permanently fix the PrintNightmare vulnerability on Windows 10 21H1, 20H2, 2004, and older versions that bumps the version number to 19041.1083, 19042.1083, and 19043.1083, respectively.
According to the documentation, after installing the update, “users who are not administrators can only install signed print drivers to a print server” to patch the vulnerability. “By default, administrators can install signed and unsigned printer drivers to a print server. The installed root certificates in the system’s Trusted Root Certification Authorities trusts signed drivers.”
Microsoft categorizes this problem as severe, and it’s recommending installing the update on all affected systems (clients and servers), starting with devices acting as print servers.
The same update is also available as KB5004946 for windows 10 version 1909. For version 1809, the update is KB5004947, and for the initial release of the operating system, the update is described as KB5004950.
You can install this out-of-band patch from Settings > Update & Security > Windows Update, and clicking the Check for updates button.
You can also get the standalone version of the update from the Microsoft Update Catalog website.